Access a Private AWS Resource
Retool Cloud relies on customer data in APIs or Databases via Retool Connect. Often these resources are protected by placing them in private subnets within a VPC. What approach should a customer use to allow Retool to access these services while maintaining existing security controls?
Pattern solution
Because Retool Cloud is running external to a customer’s VPC, the customer will need to provide an ingress mechanism. This can be done through the use of a Network Load Balancer, that provides an Elastic IP address. The NLB can then use a target group to forward the traffic to an EC2 instance, RDS instance or an Application Load Balancer that is fronting the API for example. The security group of the resource will need to allow ingress from the NLB security group. The NLB security group will need to allow ingress from the Retool CIDR range defined here. The following architecture diagram provides an example:
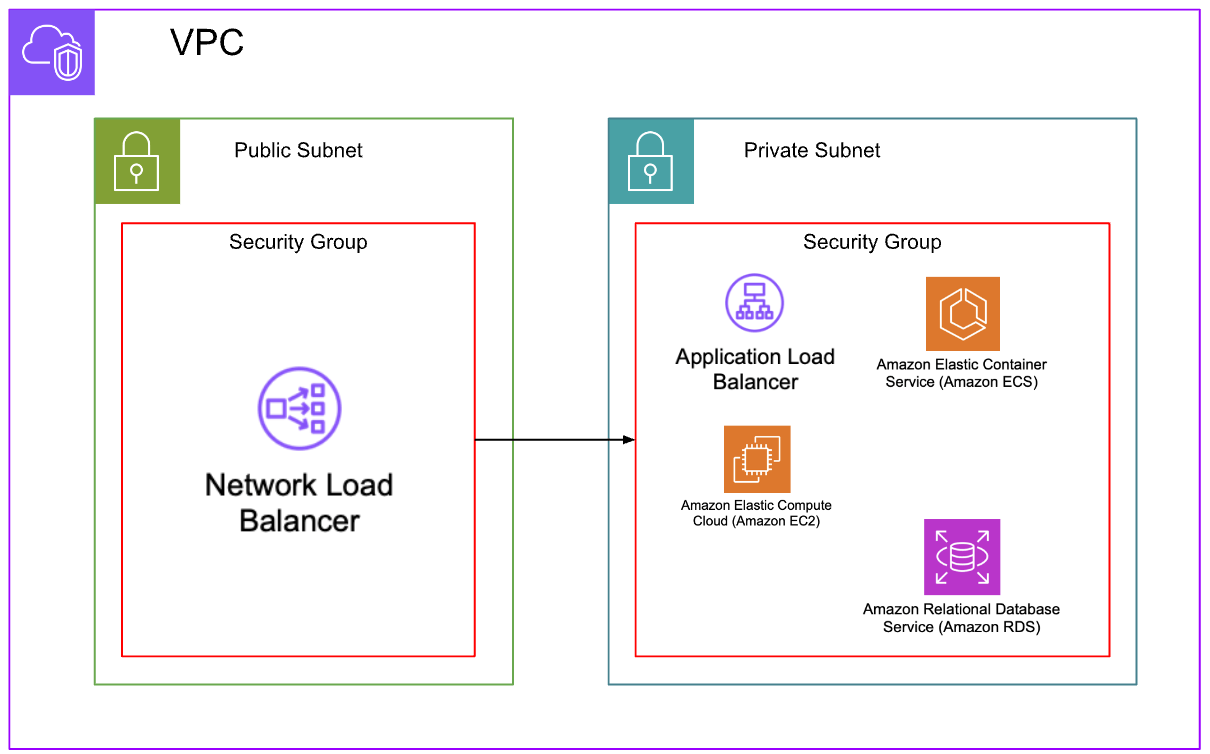
Once this has been configured in AWS, Retool Resource (e.g., REST API, Database) can be configured to use the NLB Elastic IP address.
Pattern resources
The following AWS Blog covers some of the same topics related to NLB to ALB integration.