View user audit logs
Learn how to view and query user audit logs.
| Audit Logs Availability | |||
|---|---|---|---|
| Cloud | Generally Available | ||
| Self-hosted Edge 3.36 or later | Generally Available | ||
| Self-hosted Stable 3.33 or later | Generally Available | ||
Audit logs require administrator permissions.
Retool automatically logs user actions, such as query runs and password resets. The logs include user information (such as the user ID in the audit log download, and the user's email on the Audit logs page), the action taken, and when the action took place.
You can access audit logs from either:
- The User menu on the top-right when browsing your organization.
- The Retool menu on the top-left of the app IDE.
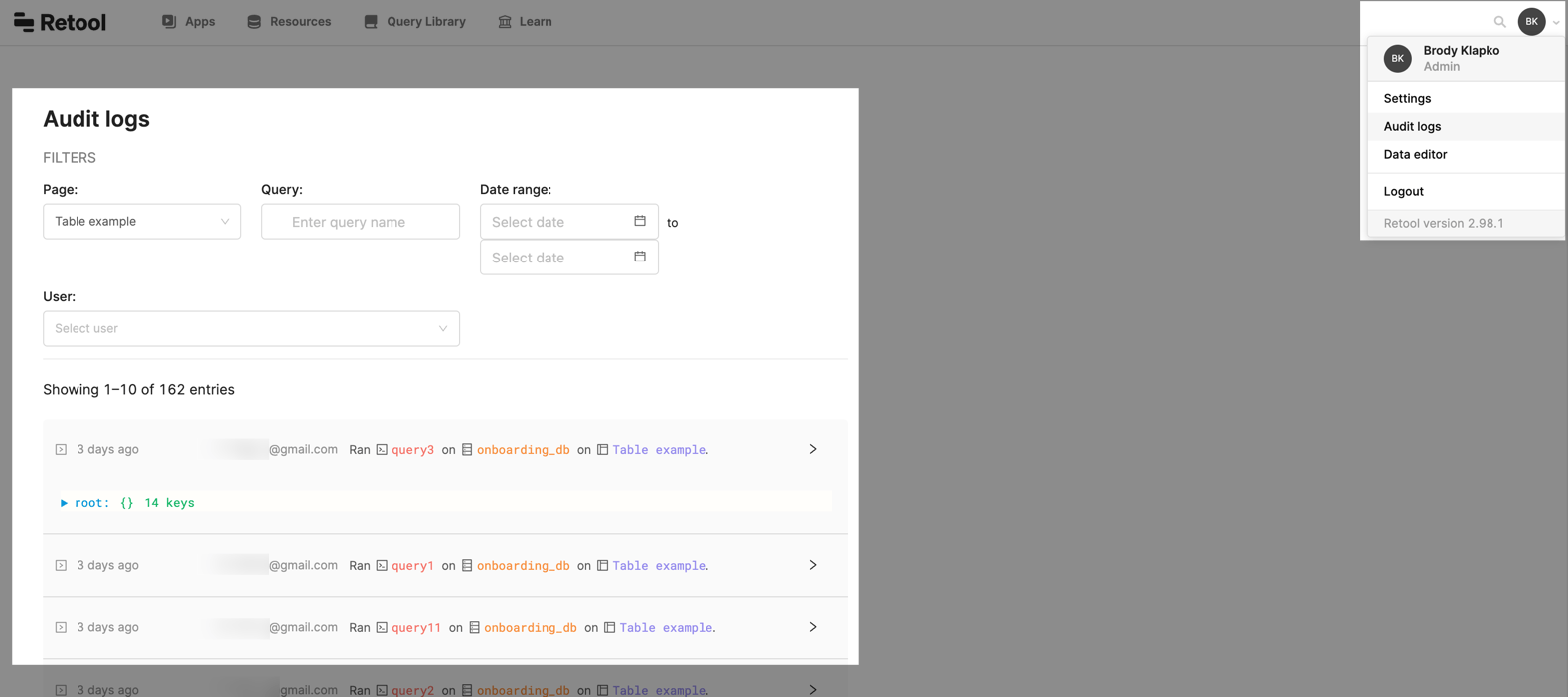
To access the audit log, visit /audit. You can see a list of all the events that occurred, information about the user who performed them (email or user ID), and the time. You can also explore more detailed information, including the exact query, the parameters passed, the user's IP address, or response time.
For a full list of events captured in the audit logs, refer to the Logged events reference page.
Audit logs for cloud instances are retained for one year. You can see the past three months of data using the Date range selector on the Audit logs page, and you can download logs for the past year. Self-hosted instances manage their own audit log retention.
Access audit logs in SQL
Access to the audit logs SQL table are only available on self-hosted instances. If you're interested in self-hosting Retool, reach out for a demo.
Self-hosted instances can use SQL to query the audit logs database table.
Query audit logs in SQL
Retool logs events to the audit_trail_events table in the postgres database of the deployment instance. You can create a PostgreSQL resource if you want to build apps and workflows to query audit log data.
The audit_trail_events table contains the following columns.
| Column | Description |
|---|---|
actionType | The type of action taken. See Logged events for possible values. |
userId | The ID of the user taking the action. |
ipAddress | The IP address of the user taking the action. |
responseTimeMs | The response time of the action, in milliseconds. |
pageName | The name of the app, module, workflow, or page on which the action was taken. |
queryName | For query actions, the name of the query. |
resourceName | For actions on resources, the name of the resource. |
metadata | Additional data about the action. |
You can join the audit_trail_events table with the users table to learn more details about the users who performed actions. For example, the following query returns records of groups created and the user who created each group.
select
u.email, u."userName", a."actionType", a.metadata
from
audit_trail_events a
join users u on a."userId" = u.id
where a."actionType" = 'CREATE_GROUP';
Export and download audit logs
If you self-host Retool, you can export and stream audit logs using SQL and stdout or by connecting to DataDog, which is supported for cloud instances as well.
Output audit logs to stdout
If you self-host Retool, set the environment variable LOG_AUDIT_EVENTS=true to output all audit log events to stdout. This is useful if you use external services to monitor and consume logs from stdout. You can set up a sidecar service that ingests these logs and set up custom monitoring in your APM solution.
Stream audit logs to Datadog and Splunk
This feature is only available on the Enterprise plan. If you self-host Retool, you must be running version 3.38 or later for Datadog and 3.114 or later for Splunk.
- Datadog
- Splunk
To configure Datadog:
- Create a Datadog API key for streaming Retool audit logs.
- Enter your Datadog API key on Settings > Advanced under Audit Log.
Logs will be sent to Datadog with service:retool-audit-log attribute.
To configure Splunk:
- Create an HTTP Event Collector (HEC) token for Retool audit logs.
- Determine the HEC URI where the logs should be sent.
- Enter your HEC token and URI on Settings > Advanced under Audit Log.
Retool sends logs to Splunk with source:retool-audit-log attribute.
Download audit logs on cloud instances
Cloud customers on a Business or an Enterprise plan can download audit logs directly from the Audit Logs page.
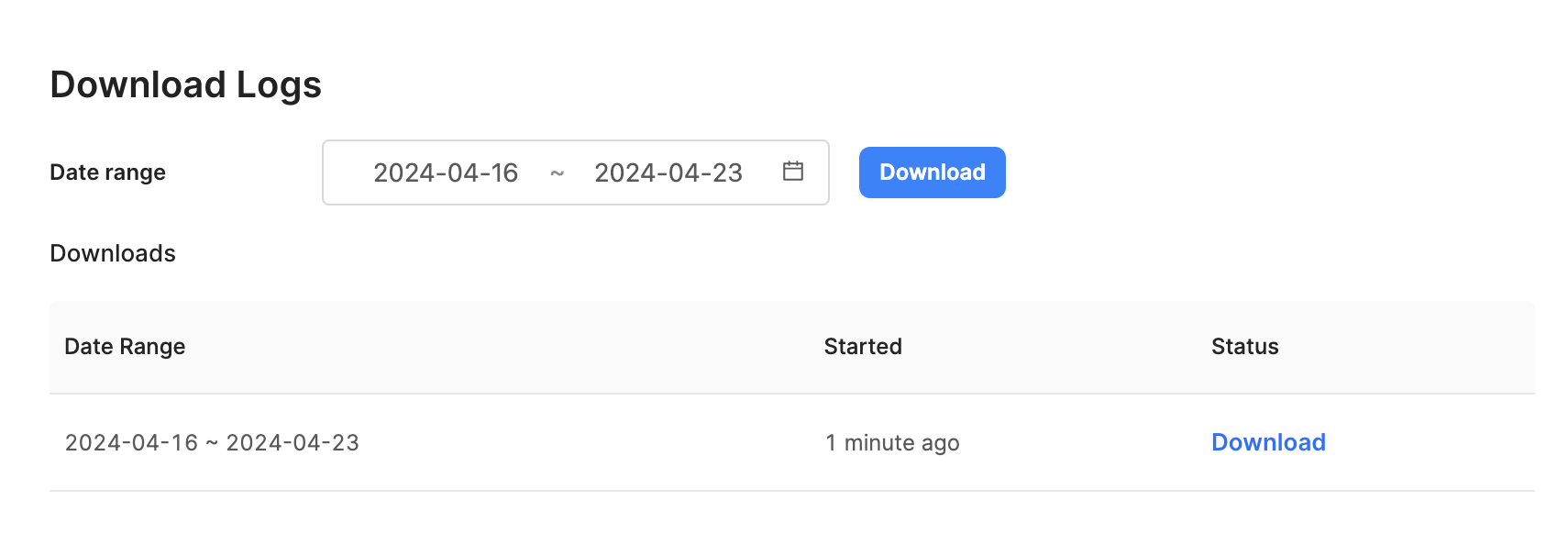
After selecting a date range and starting a download, the download job is displayed in a list with a Pending status. Once complete, a temporary link with a compressed CSV file is made available in the Downloads list. The link expires an hour after being created.
Download audit logs on self-hosted instances
If you self-host Retool and have connected to the Retool audit logs database table, you can export audit logs through the following SQL command:
\copy audit_trail_events to 'audit_logs' csv;
Hide query data from logs
You can hide parameters from logs on a per-query basis. See the query documentation for more details.
To prevent all headers in queries from being logged, enable the HIDE_ALL_HEADERS_IN_AUDIT_LOG_EVENTS environment variable. This is only available on self-hosted instances.