Manage secrets with environment variables
Learn how to use secrets to manage environment variables.
| Self-hosted Retool Availability | |||
|---|---|---|---|
| Self-hosted Edge | Generally Available | ||
| Self-hosted Stable | Generally Available | ||
Self-hosted Retool is available on an Enterprise plan only.
You can use environment variables to manage secrets like database passwords and bearer tokens. This allows you to automatically rotate secret credentials, and help protect sensitive information.
If your use case requires higher level of security, you may want to use AWS Secrets Manager or HashiCorp Vault to externally manage secrets. These integrations allow you to rotate secrets without redeploying your Retool instance.
To manage secret and non-secret environment variables through Retool's web interface, consider using configuration variables.
1. Define the RETOOL_EXPOSED_DB_PASSWORD variable
Set the RETOOL_EXPOSED_DB_PASSWORD variable to your database connection string. Depending on how you set up Retool, you might need to restart the Docker container.
To avoid leaking potentially sensitive environment variables, Retool only allows users to read environment variables with the RETOOL_EXPOSED_ prefix.
2. Create a new Postgres connection
Add a new Postgres connection and use the connection string format. Make sure to replace the database password with the %RETOOL_EXPOSED_DB_PASSWORD% variable. It should look something like this.
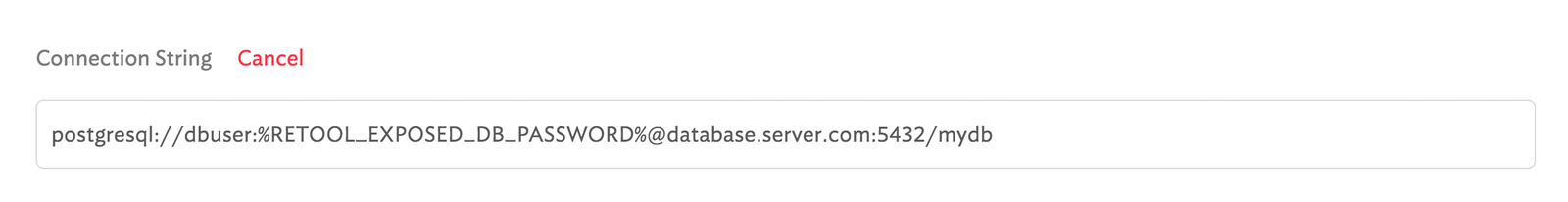
You can use environment variables like this for any field that you define. For example, you could use environment variables to configure the headers you send in API requests.
3. Save and restart the container
Click Save and restart the container.