AWS Secrets Manager
This laboratory focuses on configure Retool with AWS Secrets Manager to storage and manage secrets.
Requirements
To configure secrets management you will need:
- Amazon Account with Administration privileges to configure AWS Secrets Manager.
- Retool running on Amazon EC2
Requirements
To configure a secrets management the following is required:
- Retool Administrator permission either via Admin permission group or Role.
Steps
Following instructions per:
https://docs.retool.com/self-hosted/guides/secrets/aws
- Login to AWS Console and go to Amazon RDS > Create database. Complete the form inputs using the images below as an example.
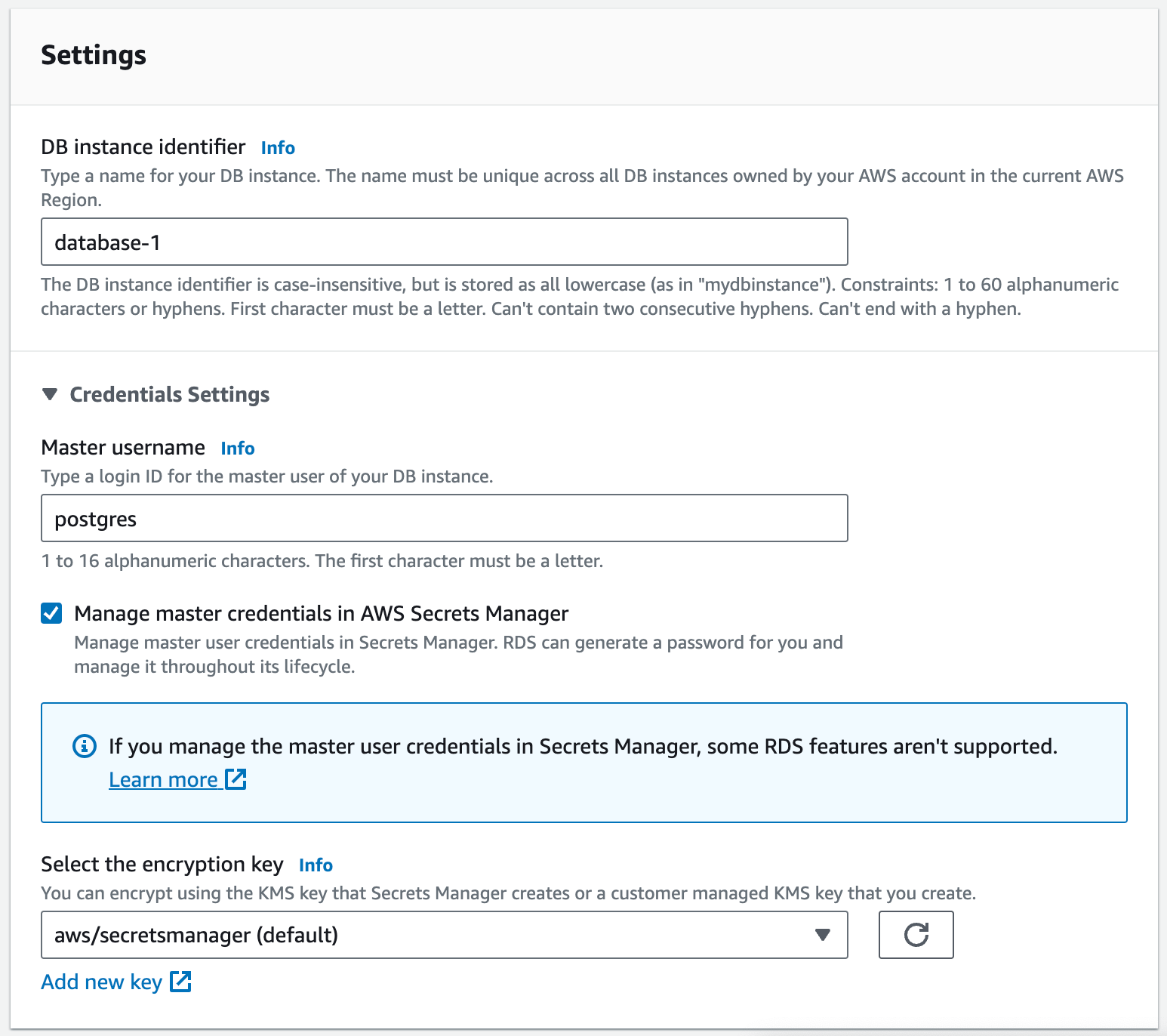
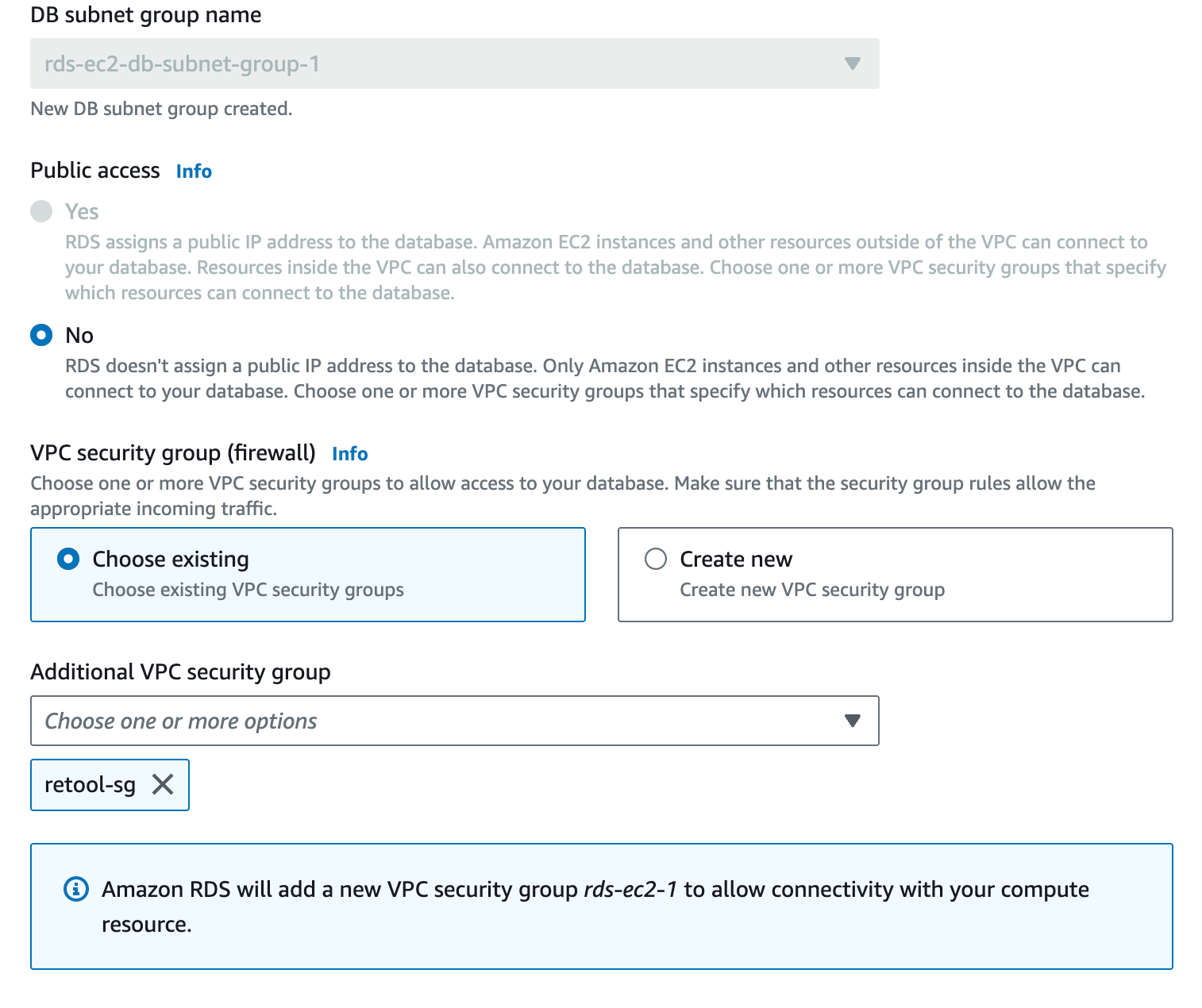
NOTE: This example assumes that Retool has been installed on an Amazon EC2 instance in the same VPC as the Amazon RDS database that will be created. If your Retool instance is running locally on your laptop, then in the section Compute resource, select Don’t connect to an EC2 compute resource. You will also need to enable Public access for Retool running locally to be able to connect over the Internet.
- Create policy by going to AWS Management Console > IAM > Policies > Create Policy.
- Select JSON and cut and paste the entry below.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"secretsmanager:GetSecretValue",
"secretsmanager:DescribeSecret"
],
"Resource": ["arn:aws:secretsmanager:[SPECIFY your Region]:[SPECIFY your AccountId]:secret:retool/*"]
},
{
"Effect": "Allow",
"Action": ["secretsmanager:ListSecrets"],
"Resource": "*"
}
]
}
- Create EC2 role using policy created previously.
- Add IAM Role to EC2 instance. Go to EC2 > Manage > Security > Attach IAM Role.
- Access Retool -> Settings -> Secrets Manager.
- Specify the
Region,Retool NamespaceandCache TTL.
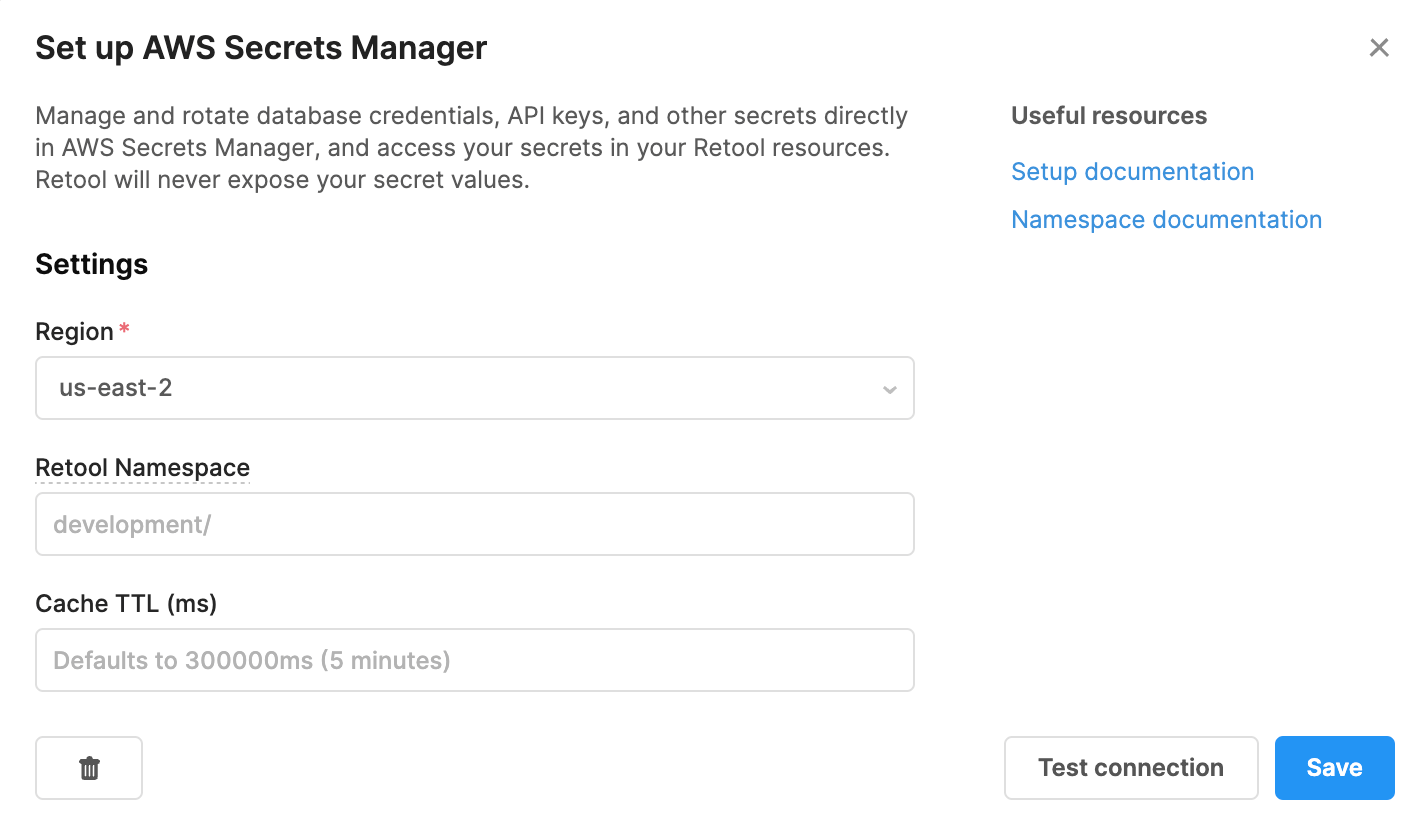
- Test the connection.
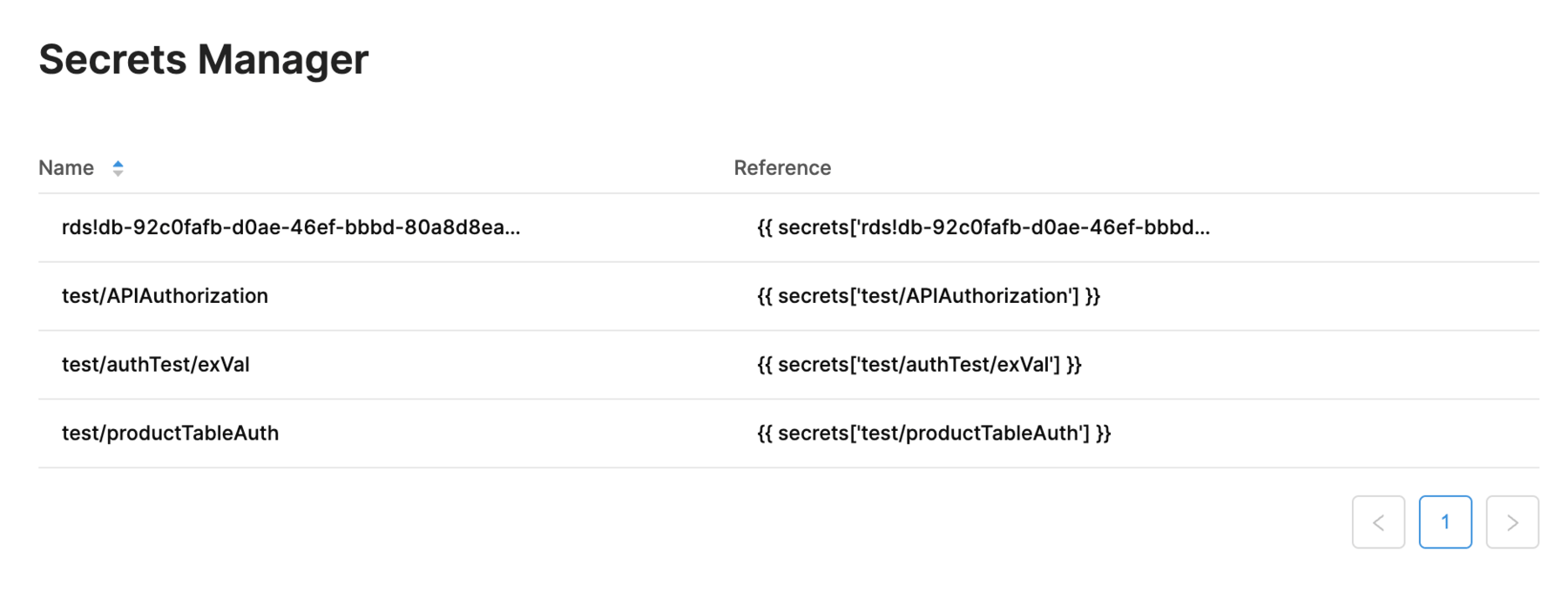
- The connection is saved and displayed at the top of the list in the following figure.
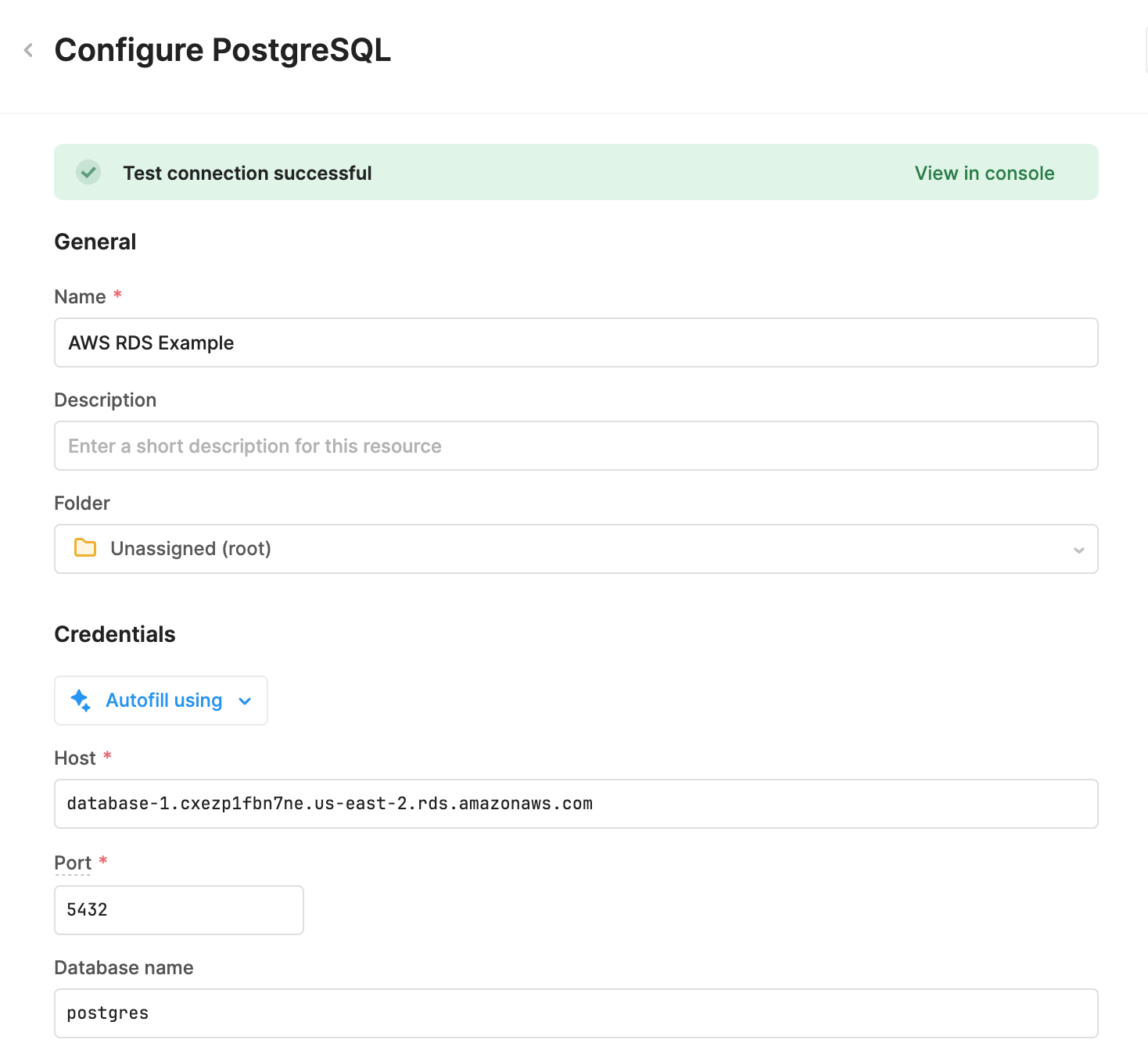
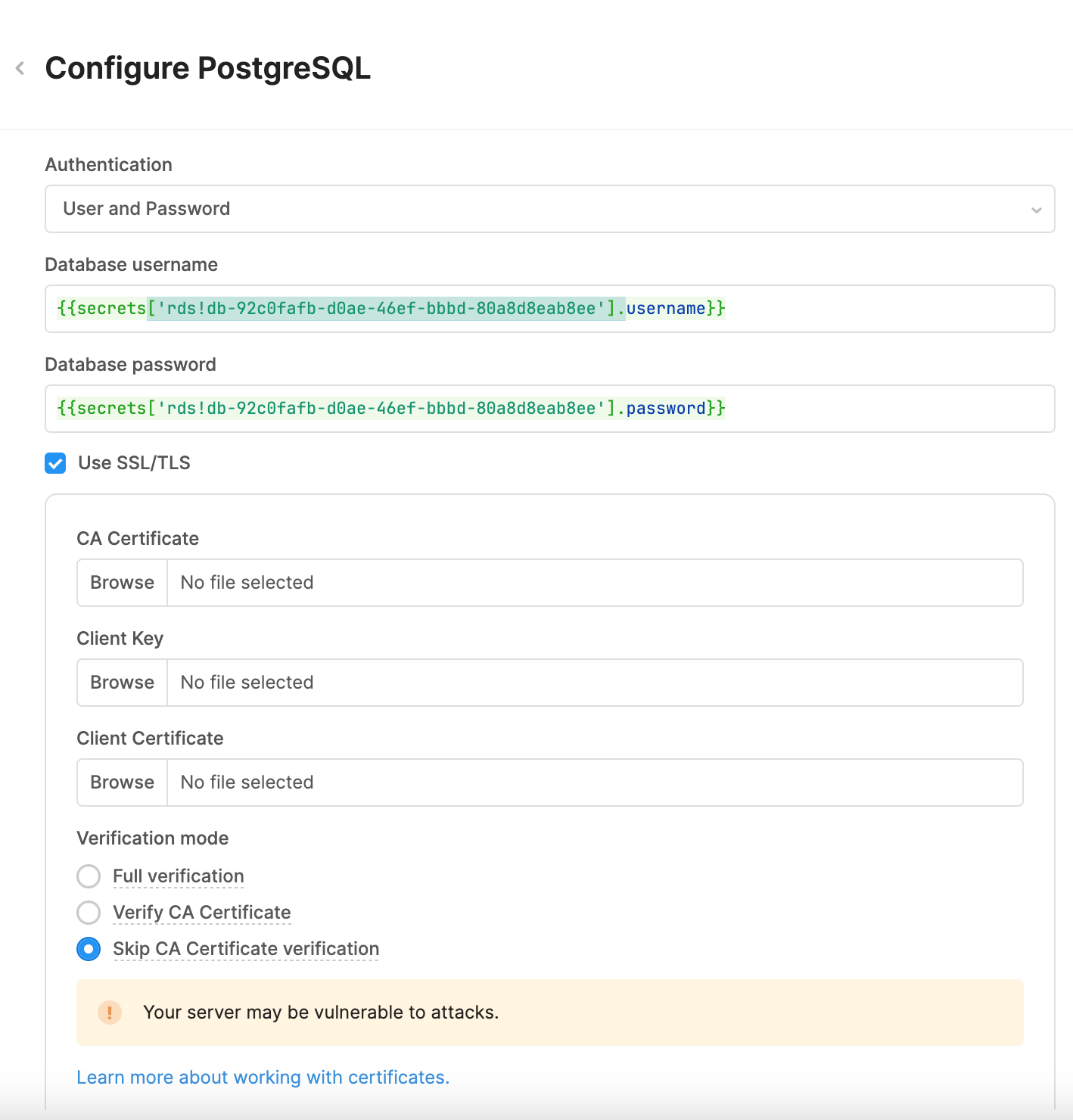
- Create a PostgreSQL Resource. Use the connection string provided when the database is started. Specify Username/Password for authentication.
- For the Username enter the following:
{{secrets.[saved_secret_name].username}}
- For the password enter the following:
{{secrets.[saved_secret_name].password}}
- The updated resource connection details should appear similar to the following:
Cleanup of Amazon RDS and AWS Secrets Manager
The following steps can be used to cleanup the Amazon RDS instance.
Delete the Resource in Retool
Go to Retool Home Page > Resources > (select Resource created previously) > … > Delete.
Delete the Amazon RDS Database
Go to AWS Console > Amazon RDS > Select Database > Actions > Delete.
NOTE: RDS will ask to create a snapshot prior to deletion. This is not necessary and can be skipped.
Delete the AWS Secrets Manager Entry
Go to AWS Secrets Manager > select the created secret > Actions > Delete secret.